Caption: AI render of an imagined DPRK developer workspace.
Is your remote dev pipeline a welcome mat for Pyongyang?
Most executives relish a talent pool without borders, but North Korea counts on that openness. What happens when the enemy doesn't pop your servers, but instead walks through the front door with a stellar resume? North Korean threat actors have weaponized the remote work revolution, turning job applications into trojan horses. North Korea no longer needs zero‑days (though they are unlikely to drop optionality in offensive tooling) when your HR portal hands them a badge. The regime’s operators pose as talented freelancers, quietly rewriting risk registers while they refactor your codebase.
North Korean groups aren’t chasing headlines; they’re chasing funding.
The Enemy Within: Building Resilience Against DPRK Developer Infiltration
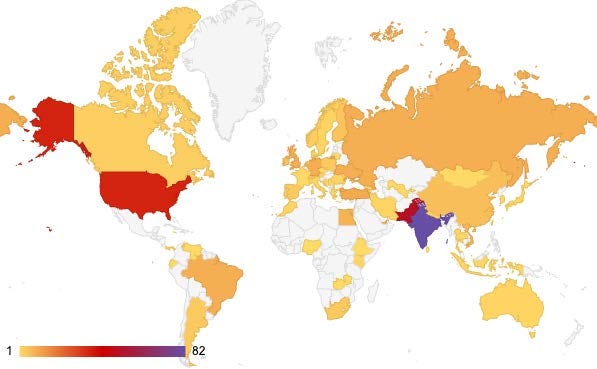
The stakes couldn't be higher for CISOs navigating this threat. Recent Recorded Future network intelligence reveals (thanks to the talented researchers in Insikt Group for highlighting) PurpleBravo operations have compromised 353+ victims across 63 countries through sophisticated developer infiltration campaigns. These aren't opportunistic attacks; they're systematic, state-sponsored operations designed to steal intellectual property, violate sanctions, and potentially establish persistent access to critical infrastructure.
Caption: Geographic locations of potential victims (Source: Recorded Future)
The risk impacts extend beyond immediate financial losses (including sending a bi-weekly paycheck to an adversary). Regulators have sharpened their teeth: OFAC now fines both the shell company and the careless hiring firm. Each paycheck routed to Pyongyang violates US and EU sanctions, risks 4 % GDPR penalties, and worse, pushes DPRK missile R&D one sprint closer to launch.
More troubling, these DPRK operators demonstrate persistence that traditional security controls struggle to detect.
The Insider Threat Evolved
Traditional insider threat models assume malicious actors emerge from legitimate employees who've gone rogue. DPRK operations flip this assumption entirely. The threat actor was never legitimate to begin with.
PurpleDelta operators maintain sophisticated personas using multiple identities on individual devices. They deploy professional-grade toolkits, including Astrill VPN (exit nodes in Dallas, for example, to spoof a US presence), AnyDesk (silent lateral moves), and CallRT monitoring systems (Pyongyang minders watch every keystroke), that rival legitimate developer environments. The quality of their work often matches or exceeds that of legitimate contractors, making detection through performance metrics nearly impossible.
These operators target specific industries with surgical precision. Cryptocurrency, fintech, and AI companies face disproportionate targeting as the DPRK seeks technologies that advance its strategic objectives. The remote developer hiring surge, up 87% post-pandemic, has exponentially expanded their attack surface.
Caption: A different AI render of an imagined DPRK developer workspace.
Beyond HR: Technical Hunt Tactics
While HR departments rightfully focus on enhanced vetting procedures (ask candidates to cover their face with a hand to expose deepfakes), security teams must assume some infiltration will occur. The question becomes: how do you detect a skilled adversary who's supposed to be there?
Behavioral analytics provide the first line of technical defense. Legitimate developers exhibit consistent patterns in code commits, work hours, and collaboration styles. DPRK operators often work unusual hours aligned with Pyongyang time zones, demonstrate coding patterns inconsistent with claimed experience levels, and avoid video calls or real-time collaboration.
Network traffic analysis reveals additional indicators. Multiple VPN connections, unusual geographic routing, and encrypted communications outside approved channels warrant investigation.
Code repository monitoring offers another detection vector. Embedded backdoors, unusual library dependencies, and modifications to security-critical functions require immediate scrutiny. Implement automated scanning for known DPRK malware signatures, including BeaverTail, InvisibleFerret, OtterCookie, and GolangGhost variants. Other operational control considerations:
Geo-fence developer VPNs and enforce corporate VPN split-tunnel deny.
Deploy YARA/Sigma/Snort rules for KimJongRAT
Instrument Git repos: alert on new .go loaders, main64.log artifacts, and mass force-pushes.
Harden payroll: screen for PingPong or PayPal accounts linked to Gmail aliases that match known patterns.
Remove blanket allow-lists for node, go, and npm run build.
Log IDE plugin installs.
Flag outbound DNS requests to dynamic DNS (DDNS) apex domains.
Control Validation That Actually Validates
Most organizations validate controls against theoretical scenarios rather than active threats. DPRK infiltration demands a different approach—one that assumes compromise and tests detection capabilities.
Purple team exercises should simulate DPRK tactics, techniques, and procedures (TTPs). This includes testing responses to developers who exhibit suspicious behaviors, validating monitoring of development environments, and assessing incident response procedures for intellectual property theft scenarios. Traditional red team engagements miss the slow-burn nature of these operations.
Endpoint detection and response (EDR) solutions require tuning for developer-specific threats. Standard configurations often allowlist development tools that DPRK operators exploit for command-and-control communications. Implement enhanced logging for development IDE use, repository access patterns, and code compilation activities.
If data loss prevention (DLP) controls are available, they need calibration for source code protection. Many organizations focus DLP on traditional data types while ignoring proprietary algorithms and development methodologies that represent core intellectual property. DPRK operators systematically exfiltrate these assets over extended periods.
Building Resilience Through Intelligence
Effective DPRK defense requires understanding evolving threat actor capabilities and targeting preferences. Recorded Future intelligence reveals these operations adapt quickly to defensive measures, requiring organizations to maintain current threat intelligence.
Indicator-based detection provides tactical value, but strategic intelligence drives resilience. Understanding DPRK economic incentives, target prioritization, and operational timelines enables proactive defense planning. Organizations in targeted sectors can anticipate attacks and pre-position defenses accordingly.
Threat hunting programs should incorporate DPRK-specific hunt hypotheses. Rather than generic anomaly detection, focus hunting activities on developer behavior patterns, intellectual property access anomalies, and communication indicators consistent with DPRK operations. This targeted approach yields higher fidelity detections with reduced false positive rates.
Caption: AI render of threat intelligence analysts collaborating on DPRK campaign analysis
Resilience to DPRK Infiltration
Implement behavioral analytics for developer populations with a specific focus on work patterns, communication preferences, and collaboration styles that deviate from established baselines.
Mandate live‑video onboarding. Ask candidates to cover their faces with a hand as deep‑fake lag exposes PurpleDelta actors.
Deploy enhanced monitoring for development environments, including IDE use patterns, repository access logging, and code compilation activity with automated alerting for anomalous behaviors.
Establish purple team exercises simulating DPRK infiltration scenarios to validate detection capabilities and incident response procedures for long-term embedded threats.
Tune EDR solutions for developer-specific threats by removing development tool allow-lists and implementing enhanced logging for tools commonly exploited by DPRK operators.
Implement source code-focused DLP controls that protect proprietary algorithms, development methodologies, and intellectual property beyond traditional data classifications.
Integrate DPRK-specific threat intelligence into security operations with regular updates on campaign indicators, targeting preferences, and evolving tactics.
Continuously emulate DPRK TTPs. Schedule weekly breach and attack simulation (BAS) campaigns mirroring PurpleBravo implants.
The DPRK developer infiltration threat represents a fundamental shift in how organizations must approach insider risk. Traditional trust-but-verify models prove inadequate against adversaries who arrive pre-compromised. Building resilience requires assuming some infiltration will occur and implementing layered defenses that detect, contain, and eject sophisticated threat actors masquerading as legitimate employees.
North Korean operators may write beautiful code, but resilience demands we kick them out before the sprint review. Waiting for incident response means you’ve already paid for the next missile test.
Caption: AI render of a DPRK ICBM launch.