Five Risk Impacts
To Improve Executive Communication
The World Economic Forum and Accenture recently released their Global Cybersecurity Outlook 2023 report, which is worth the read. Three timely executive takeaways include:
Structured interactions between cyber and business leaders are becoming more frequent – 56% of security leaders now meet monthly or more often with their board. This is rapidly narrowing the cybersecurity perception gap. However, more needs to be done to promote understanding between business and security teams to support effective action by organizational leaders.
Building a security-focused culture requires a common language based on metrics that translate cybersecurity information into measurements that matter to board members and the wider business.
Ultimately, cyber leaders must present security issues in terms that board-level executives can understand and act on. Business leaders, for their part, need to accept more accountability for operational cyber requirements to advance their organizations’ overall cyber capabilities.
Unfortunately, for most enterprise security professionals, a common lexicon to bridge between cyber and business is still elusive. Executives and Board of Directors are primarily concerned with high-level business risk (which means loss). They care little for the details surrounding bytes, malware, controllers, IP addresses, and other artifacts. Cyber professionals need to care about the details, of course, but effective communication in the language of risk requires consistent verbiage.
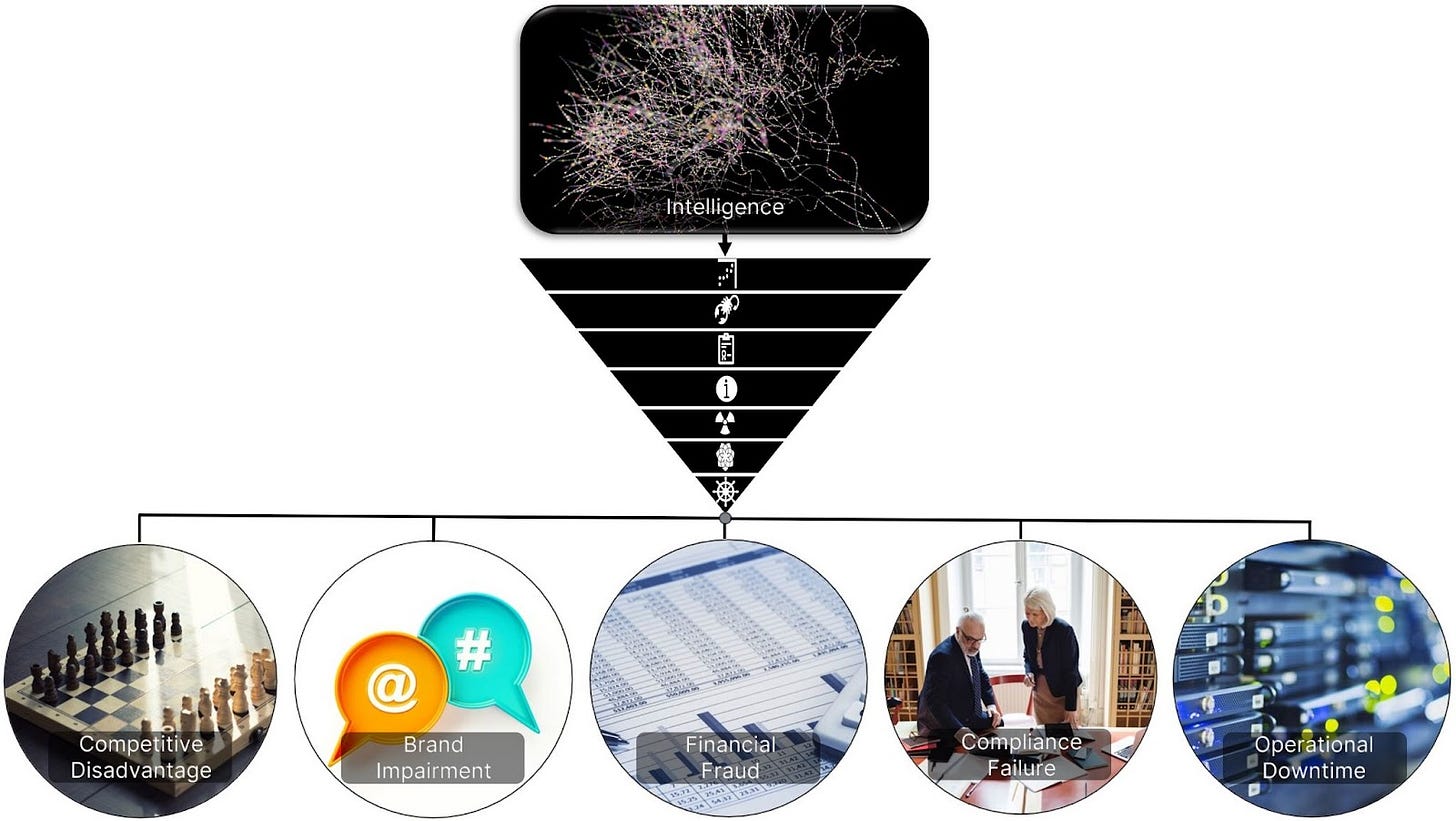
After years of substantive conversations with executives, I’m confident that all strategic intelligence leads to one (or more) of five risk impacts.
Brand Impairment
Legal or Compliance Failure
Financial Fraud
Operational Disruption
Competitive Disadvantage
Previously I discussed the Intelligence to Risk I2R) Pyramid as a framework for processing intelligence to achieve compelling risk narratives with corresponding recommendations toward action. Within the private sector, those risk stories all fit into one of these five impacts. Let’s briefly explore each label.
A competitive disadvantage is achieved when geopolitical or cyber events (often the convergence of both) result in the loss of data confidentiality or theft. As an example, going back two decades, Sino-state-sponsored groups have made a habit of compromising targets to five-finger discount trade secrets, intellectual property, and internal communications. The executive response to these types of events (whether accomplished via bribes, insiders, or digital means) ranges from “meh” to “call federal law enforcement,” usually depending on the industry. The defense intelligence base (DIB) is particularly sensitive to this type of business risk. It may take an adversary years to profit from information theft, but the long-term damage may be significant ($150M in financial loss as one example).
Like competitive disadvantage, brand impairment (sometimes labeled “reputational risk”) may not result in the immediate loss of customers or revenue. However, this risk category has the potential to drain both short-term resources and long-term profitability. Personally identifiable information (PII) breaches and associated public responses are a consistent cautionary tale. In moated industries, like credit reporting, for example, options are limited, and brand damage may be contained due to a dearth of competitors. In reputation-sensitive industries like financial services (or, ahem, crypto-currency exchanges), social media has the potential to blow an otherwise ignored security event ember into a customer loss revenue-burning fire that is difficult to quench.
Financial fraud presents straightforward outcomes for loss. Generally, for companies, the answer is smart accounting controls, but bad actors are upping their game by incorporating deepfake technology into social engineering schemes. Fraudsters are experiencing success with deep fake audio, impersonating the C-suite, and targeting foreign subsidiaries. When the CEO calls (and sounds like the CEO) and requests expedited vendor payment, most employees want to be helpful. For added efficacy, this attack pairs well with compromising an email server for a follow-up email from the CEO’s legitimate corporate email address. Business email compromise (BEC) is the most direct route to illicit millions.
Compliance failure is a risk that keeps executives up at night as the international regulatory landscape on security and privacy continues to accelerate. Cautionary tales abound. The challenge is a clear understanding of due diligence, specifically reporting requirements and the detail in definitions, thresholds, and timeframes. In the U.S., outside of industries designated “critical”, the Securities Exchange Commission (SEC) and Federal Trade Commission (FTC) wield the big sticks. Doing business in multiple countries (or with global supply chains) adds significant complexity to compliance calculations. CISOs now view personal liability insurance as table stakes primarily due to the explosion of compliance requirements.
Finally, operational downtime is a risk for any company, but transportation, logistics, manufacturers, healthcare, and emergency services are the type of industries especially sensitive to disruptions. Ransomware is the obvious threat, and controls are beginning to catch up.
Of course, explaining how adversary tactics are evolving to impact these risk categories is the heavy lifting. Second-order thinking is a requirement for risk narrative development. Enterprise risk management (ERM) is a big world. Cyber and geopolitical risk are two pieces of the pie, and they are only becoming more important for executive engagement. Using these risk categories allows cyber leaders to understand where all roads lead, and business executives can better understand the probability of future loss.