Navigating the Shifting Sands of CISO Expectations
I recently broke bread with a cybersecurity executive who had just finished his tenure at a large financial services company in Singapore. We were discussing current challenges for Chief Information Security Officers (CISOs), and he relayed that personal liability insurance is illegal in Singapore, and if found guilty of missteps, an offending CISO could be imprisoned or caned (feels a little extreme). The caning may have been hyperbole, but there’s no denying that the environment in which CISOs operate (mainly publicly traded companies) has become decidedly treacherous.
The CISO role is challenging, squeezed between aggressive expectations and significant resource constraints, particularly outside financial services. As Allen & Overy aptly convey, “Executives know that breaches are joining the list of things you can be certain of - death, taxes, and data breaches.” The CISO role is changing in response to a confluence of events that requires both organizations and CISOs to adapt for future success in cyber risk management. The focus includes heavy automation, tailored customer service, and improved storytelling.
CISO Expectations
Three primary expectations for CISOs are business acumen, regulatory knowledge, and compelling storytelling.
The first fundamental expectation from CISOs is a deep understanding of the business. While an MBA or JD might not be a prerequisite, CISOS must bridge the gap between technology, security, and risk and comprehend the business implications of their decisions.
Second, CISOs must understand current and future regulatory regimes impacting their organization and third-party relationships. New frameworks like DORA and NIS2 are renewing the focus on compliance. A legal or compliance failure has the potential to upend business operations, which is why (based on anecdotal evidence) more CISO reporting lines are moving from the CIO (Chief Information Officer) to the CLO (Chief Legal Officer) or Chief Risk Officer (CRO). Regulatory standards are lengthy and open to interpretation. Attorneys are best suited to parsing the language and need strong operational security partners to align best practices and risk reporting.
Third, governance bodies (GBs)—executives, technology/security committees, and boards of directors—are raising expectations for articulate cyber risk signaling to assist informed decisions. CISOs must build confidence in current information security program execution and recommendations toward an improved future state. CISOs are the sherpas helping GBs up the due diligence mountain.
It’s relatively easy to pontificate that successful CISOs must wear multiple hats, but HOW does a CISO create the right capabilities and execute against these expectations mentioned above? I’ll walk through the three timelessly important skills: automation, customer service, and storytelling.
Automation
“Automation” is easy to enunciate. It rolls off the tongue as a solution to all that plagues the modern enterprise. The machines will take care of it. Yet, even in this new age of GenAI, an optimally automated outcome is still complicated for all the same historically accurate reasons.
In the SaaS (and corresponding RESTful API) era, automation should involve fast and elastic storage, a couple of lines of LLM-generated Python, and, voila, beautiful data and visualizations at everyone's fingertips. In reality, we know that data is still unwieldy, regardless of whether or not the wrangling tools have improved. Data must still be sourced, collected, manipulated, normalized, correlated, enriched, and presented. Encodings, encapsulations, standards, and formatting - are part of the complexity that still causes headaches.
While automating processes and reporting is initially slow, it is foundational for every other CISO responsibility, including internal customer service and storytelling. Investing in savvy data architects and security engineers will maximize long-term information security program success. Currently, a lot of energy is spent developing SOAR decision trees, tracking the state of vulnerabilities, and removing noise from SIEM alerts. In the future, AI will replace much of these segmented systems’ relevance, replacing them with large-scale accessible security analytics. Most state change management (hosts, network, cloud, etc.) will happen before analysts and engineers report for work each morning. Humans will focus on remediating the remaining 10% long tail of unresolved issues.
Investing in automation (current and future) is also necessary for consistent and believable storytelling.
Customer Service
Rewind a decade when a CISO's primary customer was the Chief Information Officer (CIO). Outside of financial services, the mandate was generally “do more with less.” Technology was a critical business enabler, while security was a cost center. The issues with CISOs reporting to CIOs are well documented.
In 2024, there is a broader recognition that security is also a business enabler. CISOs spend time with committees and boards of directors. Beyond the CIO, executive partners include CEOs, COOs, CFOs, Chief Legal Officers, Chief Risk Officers, and Chief People Officers. CISOs partner with legal and risk in heavily regulated industries to ensure technical threats are properly translated and monitored. Success for CISOs now means effectively bridging into various lines and business functions.
For example, in 2020, NIST released NISTIR 8286 - Integrating Cybersecurity and Enterprise Risk Management (ERM), which describes challenges (e.g., “The Gap Between CSRM Output and ERM Input”) and practical tools to bridge the divide (e.g., “Cybersecurity Risk Register,” “RACI Chart,” “SWOT Analysis,” etc.).
This document will help cybersecurity professionals understand what executives and corporate officers need to carry out enterprise risk management (ERM). This includes, but is not limited to, what data to collect, what analyses to perform, and how to consolidate and condition this discipline-specific risk information so that it provides useful inputs for ERM programs. This document will also help high-level executives and corporate officers understand the challenges that cybersecurity professionals face in providing them with relevant information. Because enterprise stakeholders are accustomed to receiving reports regarding many types of risk, guidance on cybersecurity that is consistent with these other risk categories will support well-crafted and actionable risk appetite and risk tolerance decisions and statements.
However, implementing technical solutions or “identifying and analyzing the risks” is difficult in practice. These fusion (multiple stakeholders) goals represent compelling opportunities to dig into the details and execute solutions that serve the interests of multiple peer groups like ERM.
Storytelling
A Chief Risk Officer is concerned with an organization's holistic risk. Risk registers are used to track progress, reducing risk in any particular functional area. Within CSRM, the Legal or Compliance Failure risk impact is often top of mind due to the threat of significant regulatory penalties. Passing internal and external audits is a key signal for governance bodies (like the board of directors) that risk is managed correctly.
When a CRO or CLO presents to a board, a risk register heatmap or traffic light summarization may tilt toward legal and compliance. When a CISO has twenty minutes with a BoD - how is it best spent? Building confidence through storytelling - simple and concise storytelling.
Since ERM (Enterprise Risk Management) communicates the results of risk register updates, a valuable opportunity exists to inform the board of migrations in residual risk, specifically across the other four risk impacts - financial fraud, operational disruption, brand impairment, and competitive disadvantage. Operational disruption is also top of mind due to the accelerating headlines from ransomware victimization, but the remaining three risk impacts still need to be understood.
A recently updated I2R Pyramid reminds us how intelligence can be used as an originator for impactful risk narratives.
Recent reporting from Recorded Future’s Insikt Group on SolarMarker documents four years of malicious tactic evolutions (e.g., from 350 MB payload files to decoy dishwasher manuals), highlighting the need for intelligence and security practitioners to iteratively traverse the pyramid, even for a single threat implication.
As previously mentioned, broad visibility into cyber events coupled with an ability to explore threat implications and rigorously surface associated security control gaps is valuable for any organization at the practitioner level. Identifying associated risk impacts becomes critical to CISO storytelling efforts.
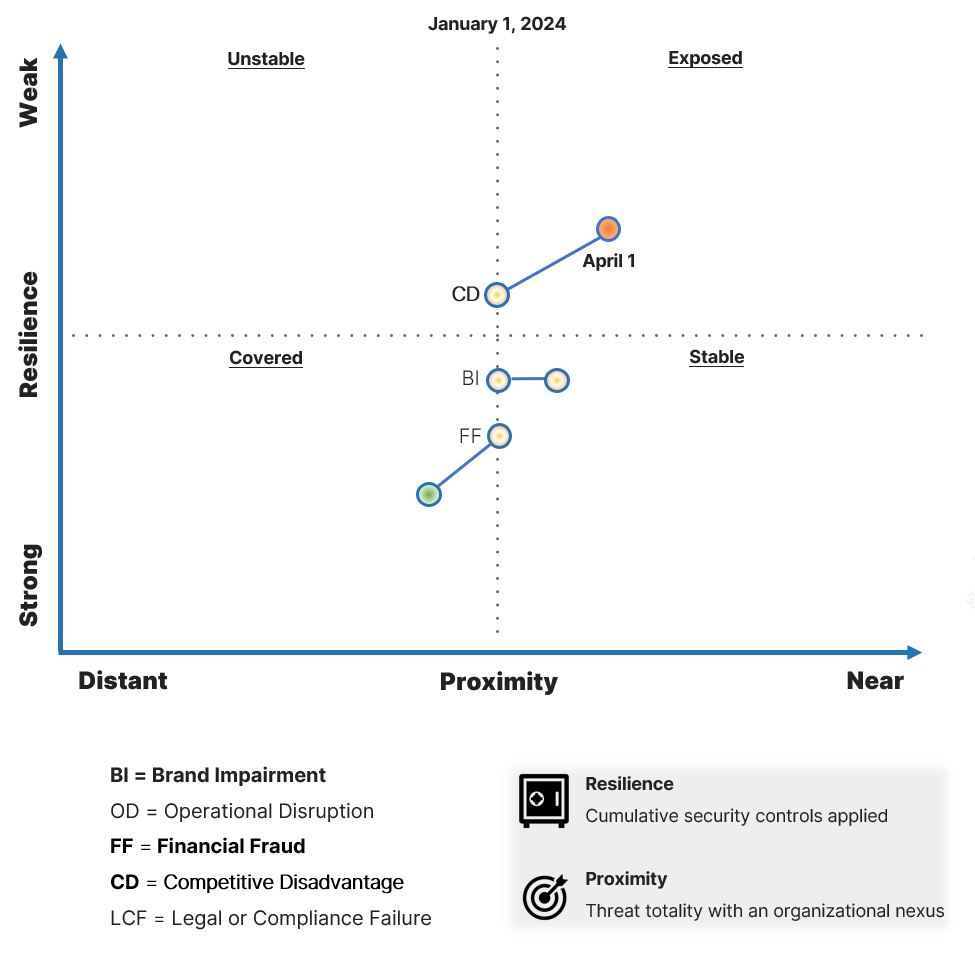
Finally, CISOs need the right storytelling vehicles to engage governance bodies quickly. A threat proximity and resilience graph helps tell the last-mile risk impact story. Again, governance bodies are already likely to be reviewing aggregate heat maps derived from risk registers, but because (as NIST so eloquently articulates) the transition from CSRM outputs to ERM inputs is difficult, much is lost in translation.
This chart gives governance bodies a better understanding of the juxtaposition between threat-driven risk and corresponding operational resilience.
Conclusion
As CISO expectations continue to expand - successful CISOs will double down on people, processes, and technology that facilitate improved CSRM analytics, help drive better outcomes in adjacent business units (e.g., GRC or Legal), and strengthen storytelling that drives more confidence in governance bodies.